Author:
(1) Yigit Ege Bayiz, Electrical and Computer Engineering The University of Texas at Austin Austin, Texas, USA (Email: egebayiz@utexas.edu);
(2) Ufuk Topcu, Aerospace Engineering and Engineering Mechanics The University of Texas at Austin Austin, Texas, USA (Email: utopcu@utexas.edu).
Table of Links
Deterministic Baseline Policies
Temporally Equidistant Prebunking
V. DETERMINISTIC BASELINE POLICIES
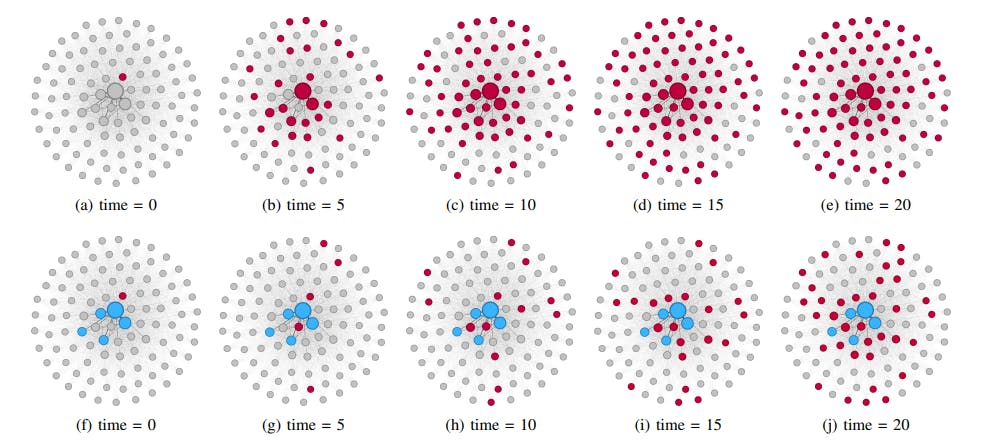
We start our analysis by introducing two baseline deterministic policies with feasibility guarantees. The first of these approaches is called early response, described in Algorithm 1. In this policy, we provide the prebunks as soon as a new misinformation is spotted in the local neighborhood of the user.
It is clear that under Assumption 3, Algorithm 1 ensures that the feasibility condition 12c holds, which we can show
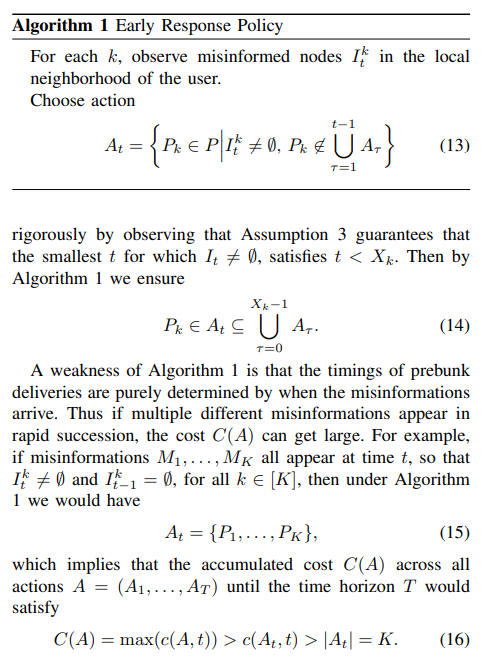
Thus, the accumulated cost over time is lower bounded by the number of simultaneous misinformation appearances.
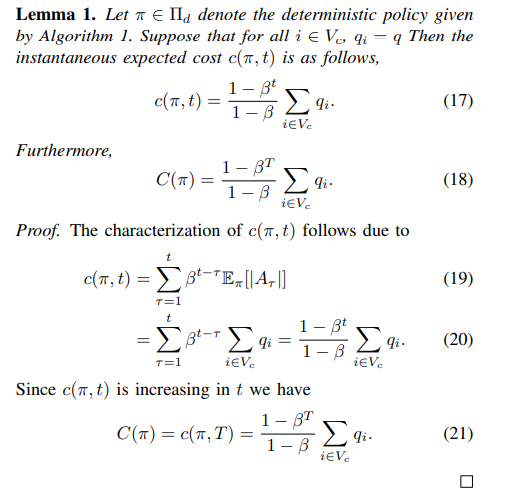
Given that the misinformation generation probabilities are constant across time, it is also possible to provide an exact closed-form expression for the policy cost of Algorithm 1, which can be seen in Lemma 1.
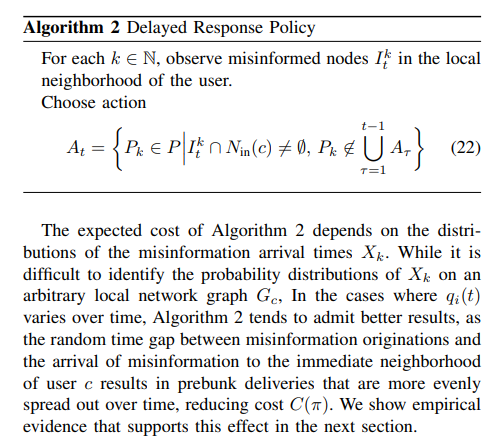
As a second baseline algorithm, we test introducing a random time gap between the origination of each misinformation and the delivery of their corresponding prebunks. One way to achieve this time gap with a deterministic policy is to always wait until the misinformation arrives at a node neighboring the central user c before providing user c with a prebunk. We call such policy the delayed response policy and provide a description of it in Algorithm 2. As was the case for Algorithm 1, Algorithm 2 also guarantees the feasibility condition 12c.
This paper is available on arxiv under CC 4.0 license.